Imagine this scenario: You're a product manager and your team needs to build an internal dashboard, designed to give your customer service team quick access to user account details, transaction histories, and support tickets.
When managing customer data, security isn't just a checkbox—it's a critical pillar of your business integrity and customer trust. Appsmith is the leading open-source platform for building business applications, with powerful tools to safeguard your customers' data. But, a system is as secure as the way it's built, while Appsmith provides multiple ways to secure your apps, you still have control over it's runtime, access, and application business logic.
This article will guide you through essential strategies to enhance data security in your Appsmith applications.
Why Data Security Matters in Enterprise Applications
Before diving into specific practices, let's consider why data security is crucial:
- Trust: Secure handling of data builds and maintains customer trust.
- Compliance: Many industries have strict regulations regarding data protection (e.g., GDPR, HIPAA, SOC2).
- Reputation: Data breaches can severely damage a company's reputation and lead to significant financial losses.
- Competitive Advantage: Strong security measures can differentiate your business in the market.
Best Practices for Securing Customer Data in Appsmith
1. Implement Robust Authentication
Besides providing standard username/password authentication, user management, multiple roles and security by default, you can authorize users into your Appsmith apps using popular SSO authentication protocols like SAML and OpenID Connect with multiple providers like Azure Entra ID (Active Directory), Okta, Auth0, Ping Identity, Amazon Cognito, and many more, and also you can integrate any authentication method that uses OAuth 2.0.
2. Streamline User Management with SCIM
System for Cross-domain Identity Management (SCIM) provides a standardized way to automate the exchange of user identity information between identity domains, or IT systems, and we support SCIM for multiple providers like Azure Entra ID (Active Directory), OKTA, Auth0, AWS Cognito and much more. Being able to bring your organization's existing users, roles, groups and security policies.
Implementing SCIM enhances security by ensuring that user access is always up-to-date and consistent with your organization's current structure and policies, here you can find the documentation on how to integrate SCIM with multiple providers, and here's an example on how to implement SCIM with Azure:
3. Manage User Permissions Carefully by Implementing GAG
Granular Access Control (GAC) in Appsmith allows you to specify precise access permissions for every resource within your Appsmith instance. This includes applications, users, workspaces, queries, and more. Here’s a quick overview of how GAC works:
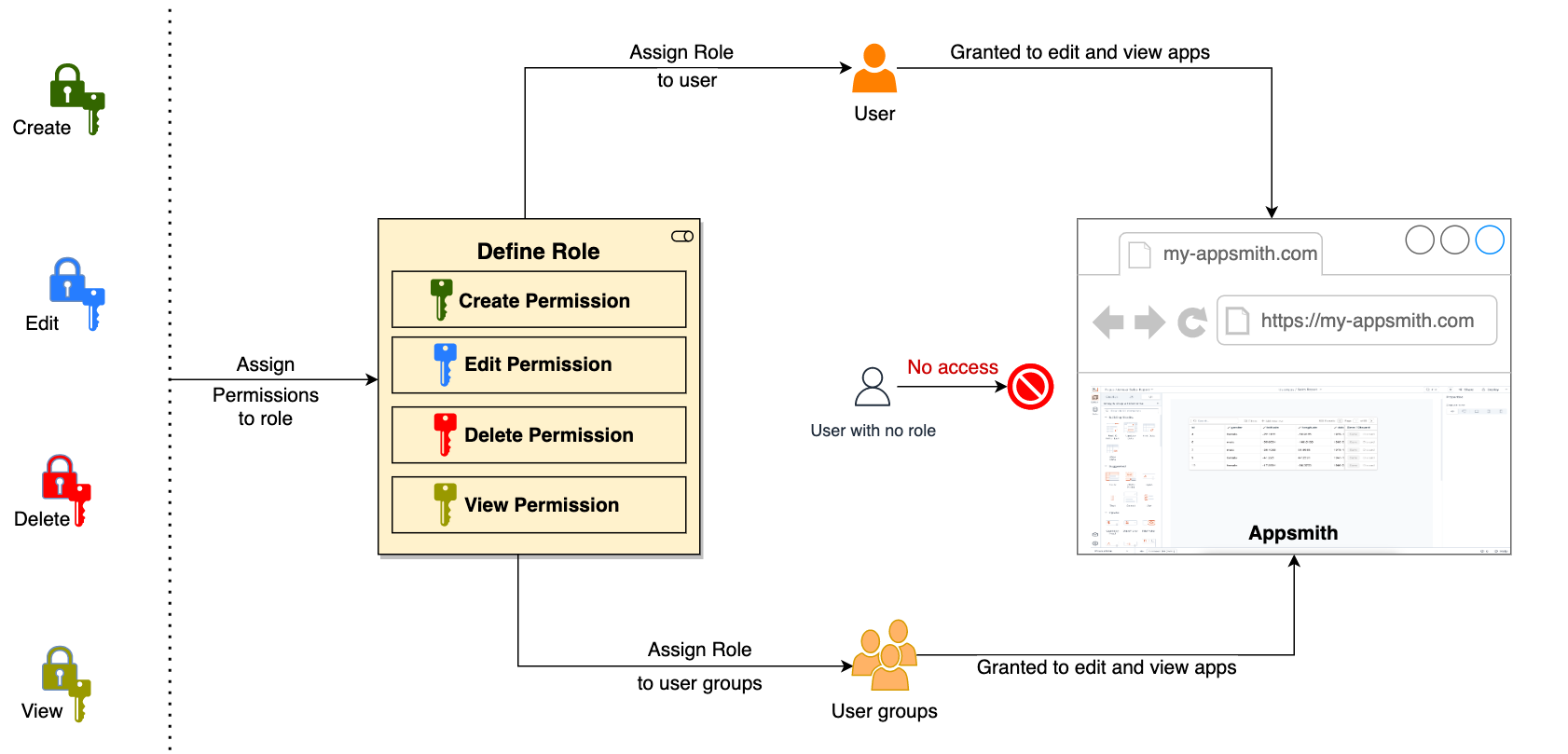
GAC in Appsmith operates at multiple levels, allowing for fine-tuned control:
- Instance Level: Control who can manage users, groups, and global settings.
- Workspace Level: Manage access to workspaces based on Roles, User, or Groups.
- Application Level: Set permissions for who can view, edit, or manage specific applications, but also you can define access to each individual widget of functionality by role by programmatically define your own business logic with Javascript.
- Page Level: Control access to individual pages within an application.
- Query/API Level: Restrict who can view or edit specific queries or API calls.
This multi-level approach ensures that you can precisely control access based on user roles and responsibilities. By implementing GAG and regularly auditing user permissions you can ensure to a secure access to your Appsmith apps. The following video explains how to use Granular Access Control at the app level to define your secure access rules and business logic
3. Secure Your API Connections
Use HTTPS and authenticated methods for all API connections, we provide a layer for Authenticaded APIs for you where we securely store API keys, secrets so they can't be retrieved again. Use this datasource to create queries within the same API, sharing common settings such as base URL, authentication, headers, and more, thereby minimizing redundant configurations.
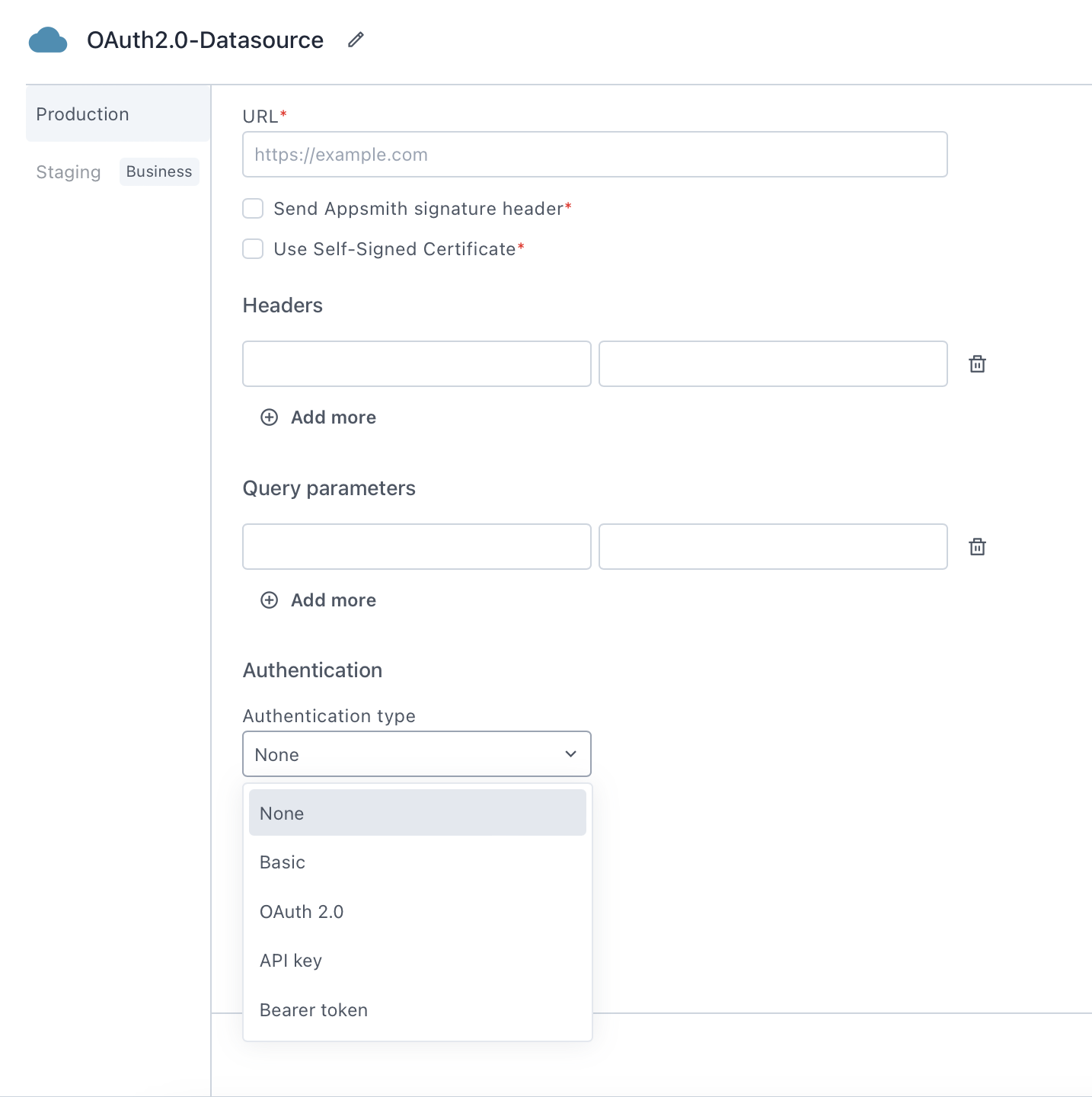
Another secure mechanism to implement APIs is using OAuth. Appsmith provides and supports all types of OAuth 2.0 authorization mechanisms, including defining the Grant type, Authorization URL, Access Token URL, Client ID, Client Secret, Scopes, and other relevant parameters required for integrating APIs that use OAuth 2.0 as an authentication method.
4. Monitor and Log Activities
The Appsmith audit log is a paper trail of all notable activities on an Appsmith instance. It automatically captures and displays events by recording what activity was performed, who performed it, and when it occurred. We strongly recommend activating it and using it for security purposes.
There are several kinds of events that are logged:
- App-specific activity
- Changes to pages
- Datasource configuration
- Query configuration and execution
- Deleting apps
- Changes to Administrator settings
- Instance configuration changes
- User sign-up and login activity
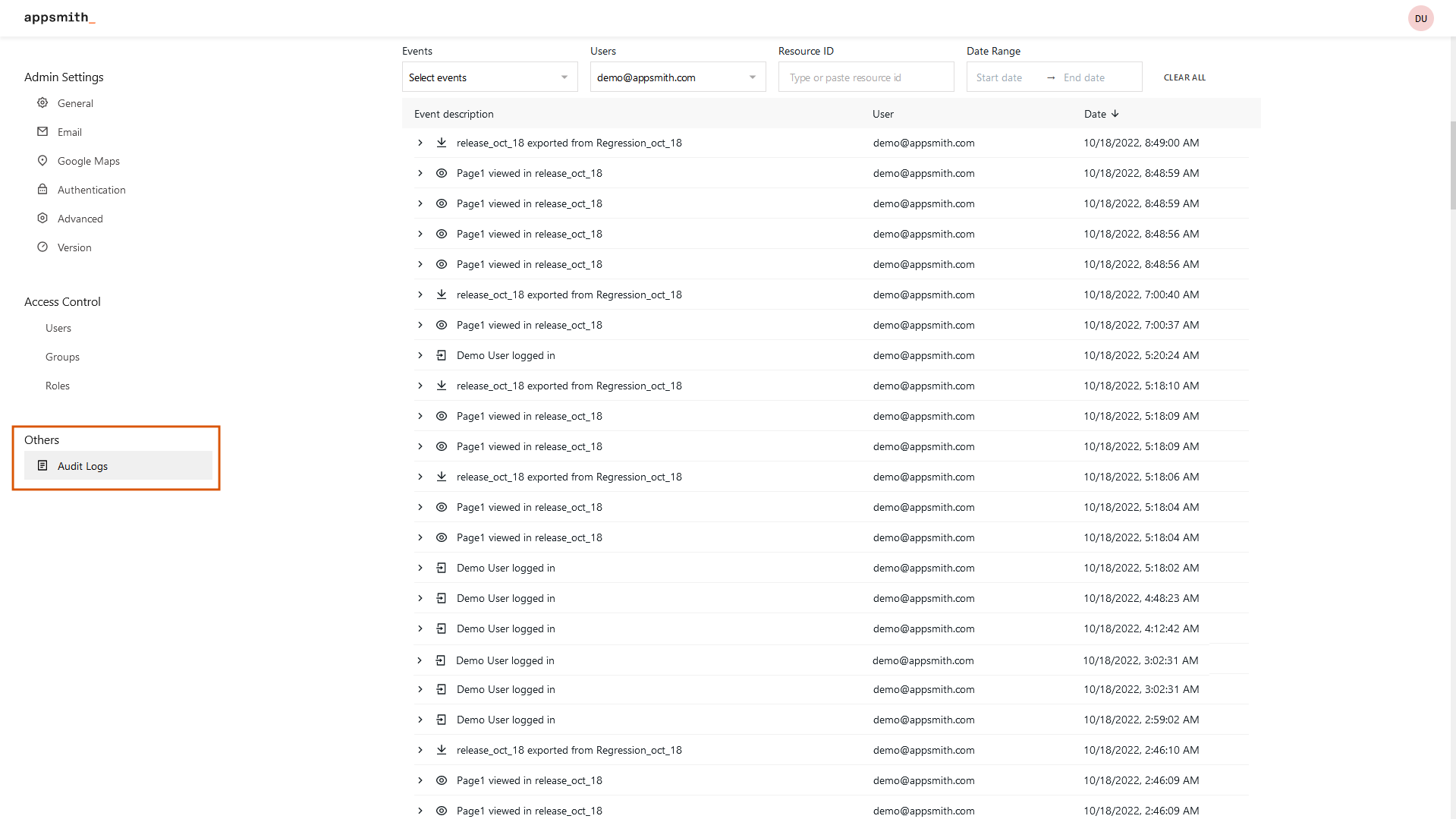
We strongly recommend regularly reviewing your logs for suspicious activities. If you want to learn more about the data you can see on the activity logs and how to enable it, visit this page
5. Keep Your Appsmith Instance Updated
Regularly updating Appsmith to the latest version can benefit from security patches and improvements, here's a guide on how to upgrade your instance, also, stay informed about security announcements from the Appsmith team by joining our Discord channel and subscribing to our Youtube channel.
6. Other recommendations
- Perform periodic security assessments of your Appsmith applications.
- Train your development and operations teams on security best practices.
- Foster a culture of security awareness within your organization.
- Develop and maintain an incident response plan.
-
Regularly test your plan to ensure readiness in case of a security breach.
Actionable Next Steps
- Assess Your Current Security Posture: Review your existing Appsmith applications against the best practices outlined above.
- Prioritize and Plan: Identify the most critical areas for improvement and create a roadmap for implementing enhanced security measures.
- Implement Changes Incrementally: Start with quick wins like enabling logs and updating to the latest Appsmith version.
- Document and Train: Create clear documentation for your security practices and conduct training sessions for your team.
- Monitor and Iterate: Continuously monitor your security measures and be prepared to adapt as new challenges emerge.
Conclusion
Securing customer data in Appsmith applications is an ongoing process that requires vigilance, expertise, and commitment. By implementing these best practices and maintaining a proactive approach to security, you can significantly reduce the risk of data breaches and build trust with your customers. Remember: robust security isn't just a feature—it's a fundamental requirement for success.



